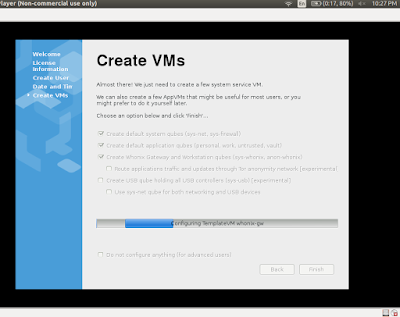
1. Chromecast is a 2.83-inch (72 mm) HDMI dongle ,a digital media player developed by Google that plays audio/video content on a high-definition display by directly streaming it via Wi-Fi from the Internet or a local network. Users select the media to play using mobile apps and web apps that support the Google Cast technology. Alternatively, content can be mirrored from the Google Chrome web browser running on a personal computer, as well as from the screen of some Android devices.This post further brings you screen shots of the Chromecast setup as I set it up on one windows 8 Laptop...sadly it doesn't have a straight setup for UBUNTU OS...though I have seen few forums wherein a plugin mention in regular chrome browser would set the cast working...but alas not tried that...here it is a simply setting it up on Windows 8.
Step 1 : As you plugin the chromecast powered by USB Power in the HDMI slot ,you get a similar looking screen.
As you click the above link you get a download setup file...around 800 kb...download that and your installation begins....
Typical Next Next.....
You get the device number as detected by the Laptop machine
Once connected a unique code is seen as below on the TV...just confirm that you see the same on your PC too as shown further below :
Unique code replicated on Laptop screen as below :
Click on
That's My Code and continue as seen below :
Seen connecting to the network SSID
Setting up the Device on joining the network
and you are ready to cast :
The first time the device is ready to cast,expect recent update on the Chromecast dongle like seen below...likely to take few minutes...mine took 7-8 minutes
Updating still....12%
Updating still....61%
Updated and now applying updates
and the first look of the device on way to cast a Youtube stream as below :
What do I cast first ?...off course Rajinikanth....:-)
Few things to ponder and for info first time users :
- Why is not ready for Opensource OS?
- Works equally ready with Android devices with ease
- Does not work on a Windows OS running in Virtual Box/Machine.
 https://orcid.org/0000-0002-9097-2246
https://orcid.org/0000-0002-9097-2246