1. Even if one is not doing anything wrong, he is being watched and recorded in real time as Edward Snowden revealed few years back. Most Internet users value online anonymity,
with majority saying they have taken steps to remove or mask their
digital footprints, and reporting that they have taken steps
to avoid being observed by specific people, organizations, or
governments.Whonix is a Debian GNU/Linux based security-focused Linux distribution which aims to provide privacy, security and anonymity on the internet. The operating system consists of two virtual machines, a "Workstation" and a Tor "Gateway", running Debian GNU/Linux. All communications are forced through the Tor network.This post gives you screen-shots of installation and execution of the virtual appliances involved.
2. The Gateway VM is responsible for running Tor, and has two virtual network interfaces. One of these is connected to the outside Internet via NAT on the VM host, and is used to communicate with Tor relays. The other is connected to a virtual LAN that runs entirely inside the host.
3. The Workstation VM runs user applications and is connected only to the internal virtual LAN, and can directly communicate only with the Gateway, which forces all traffic coming from the Workstation to pass through the Tor network. The Workstation VM can "see" only IP addresses on the Internal LAN, which are the same in every Whonix installation.
3. The Workstation VM runs user applications and is connected only to the internal virtual LAN, and can directly communicate only with the Gateway, which forces all traffic coming from the Workstation to pass through the Tor network. The Workstation VM can "see" only IP addresses on the Internal LAN, which are the same in every Whonix installation.
4. Download the two virtual machines ie the Gateway and the workstation from https://www.whonix.org/wiki/VirtualBox
5. Once you download the two machines as above from the link in reference,the following screen-shots will assist you in installation of the same.The two downloaded files are seen below :
Instead of typically creating a virtual machine and then mounting a vdi,in this case more simply we have to just import the .ova appliance,rest is in auto mode.
NextNext
Agree to the T&C
Next
Will take few minutes loading
Next
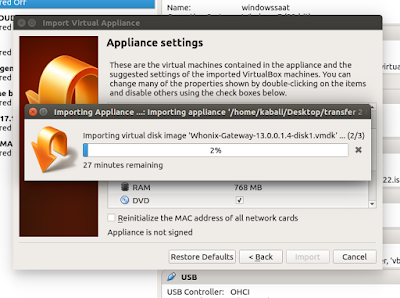
Import
Agree again
Import appliance of the workstation
Just click both with the start button...and the machine start
Next
Next
Next
Ok
Updated TOR download
Here we see the IP address relating to Budapest Hungary....and thats surely not the user....:-)
 https://orcid.org/0000-0002-9097-2246
https://orcid.org/0000-0002-9097-2246