1. Vide my last post about installing Burp Suite here ,now I move ahead to configure your browser in order to redirect all HTTP/S requests through Burp Proxy, instead of the actual target website. In my case here I am configuring a Mozilla Browser with proxy host address to 127.0.0.1 and the proxy port to 8080 , for both HTTP and HTTPS.The typical configuring of browsers is more or less common with major browsers with minor differences in interfaces.Here next I place you screen shots as I surfed a redirected traffic both for http and https via Burp Suite.First steps to configure Mozilla followed by screen shots :
Configuring Mozilla Firefox
- Click Firefox menu and then Preferences.
- In the Advanced options, under the Network tab, click on connection Settings.
- Select Manual proxy configuration.
- Enter the proxy host address as 127.0.0.1 and the proxy port as 8080.
- Select Use this proxy server for all protocols.
- Make sure to remove all exceptions from the No Proxy for field.
- Click OK and close.
- In the Advanced options, under the Network tab, click on connection Settings.
- Select Manual proxy configuration.
- Enter the proxy host address as 127.0.0.1 and the proxy port as 8080.
- Select Use this proxy server for all protocols.
- Make sure to remove all exceptions from the No Proxy for field.
- Click OK and close.
2. So now you have a working installation of Burp Suite and your browser is properly configured to intercept all requests.Now to test go to the browser, enter any http://www.****** site in the address bar and press Enter . If all is well, Burp Proxy should intercept this request. In Burp Suite,go to the Proxy and Intercept tab and verify that the web request is waiting for your approval.Ensure tha the Intercept on button is enabled; click on it and allow the request to transit through Burp by pressing Forward in Burp Suite Interface. Now in the browser, you should see the http page you entered in address bar.
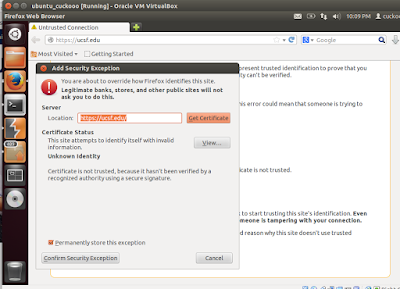
Now try a https site and you are bound to see this warning as seen below in the screenshot.You will be presented with a This Connection is Untrusted page.In such a case, you are required to manually approve the connection by clicking on I Understand The Risks, then Add Exceptions... and Confirm Security Exception. To make sure that Burp Proxy is actually causing the warning, you click on the certificate status View... and see that the certificate belongs to PortSwigger CA as seen below in one screenshot.
PortSwigger CA certificate
This setup means that Burp Suite is now ready for use as the traffic is being redirected as desired as per configuration....
 https://orcid.org/0000-0002-9097-2246
https://orcid.org/0000-0002-9097-2246