1. Skipfish is an
active web application security reconnaissance tool. It prepares an interactive sitemap for the targeted site by carrying out a recursive crawl and dictionary-based probes. The resulting map is then annotated with the output from a number of active security checks. Skipfish is fast and easy to implement and can perform a robust scan of any website providing a lot of security tests, like
php injection, XSS, format string vulnerabilities, overflow vulnerabilities, file inclusions and lot more categorized into high risk, medium risk and low risk issues. Skipfish also provides summary overviews of document types and issue types found; and an interactive sitemap, with nodes discovered through brute-force denoted in a distinctive way.
2. The first thing that you should do is download the latest version of Skipfish here:
http://code.google.com/p/skipfish/downloads/list
3. The following screenshots show a stepped way to run and use this tool...
4. As u download the file,you move to the terminal and cd to the place you have downloaded the file.Type the following command to
unzip the ,tgz file.
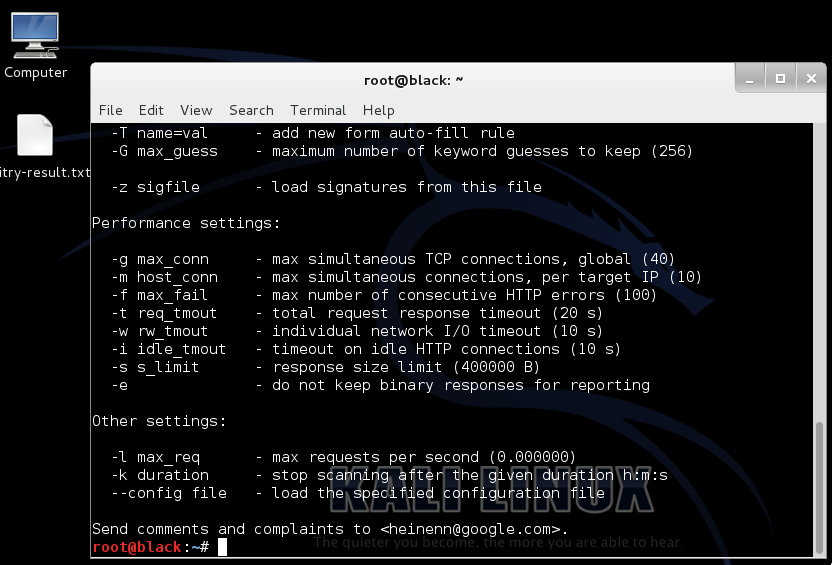
5. There are pleothra command options available in Skipfish against a
target website using a custom wordlist, enter skipfish, select your
wordlist using the
-W option followed by the location of the wordlist,
select your output directory using -o followed by the location, and
finally the target website.
Skipfish –o (output location) –S (location of wordlist) (target site)
The following example shows a scan using a wordlist called
medium.wl on
securityblogger.com. Skipfish will create a folder called
Skipfishkaoutput on the desktop. This is run using the keyword
skipfish, –o /root/Desktop/Skipfishkaoutput to specify the location to which send the output, -
W /root/Desktop/medium.wl to specify the location of the dictionary and
http://www.thesecuirtyblogger.com as the target to scan against.
So in the example that I take here,you need to type the following at the terminal :
It is also seen that the default Skipfish dictionaries will not run when using the –W command. You can copy a default wordlist and remove the read-only in the first line of the list (#ro) to run as a custom wordlist. This is shown in the following screen-shot:
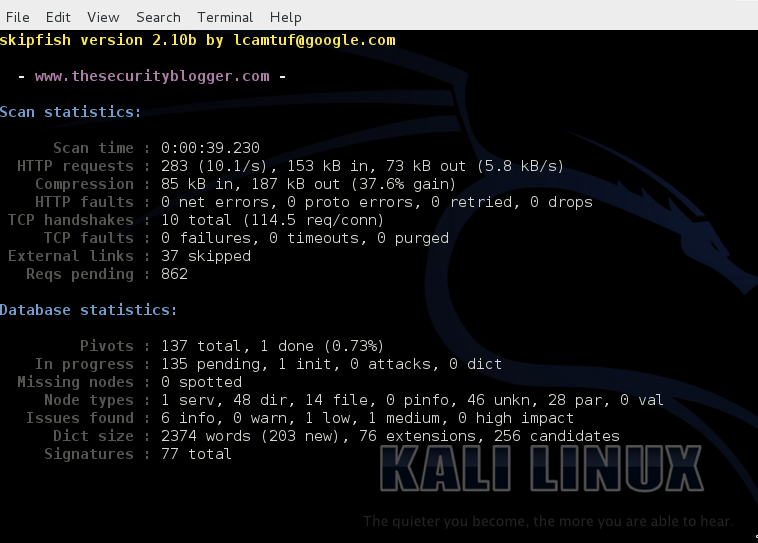
Once the scan is complete or if you end it early, Skipfish will generate thousands of output files in the location specified when using the –o option to designate an output folder.To see the results, click on the index.html file, which will bring up an browser. You can click through the drop-down boxes to see your results.
The tool is pretty powerful indeed...can be gauged from the following screen shot of a news site that says that professional criminals used this tool to hack a financial site... :-)
 https://orcid.org/0000-0002-9097-2246
https://orcid.org/0000-0002-9097-2246